- 0 Posts
- 91 Comments

Gotta say, I love the idea behind this project, and it’s great you’re reaching out to this community here. I haven’t run it myself yet, but it looks great, and the feature list is massive.
Couple questions really stopping somebody like myself from setting up an instance though.
-
It’s not “just” a launcher, and it’s not quite a distribution platform. Is this mostly geared towards people playing the same game on multiple machines?
-
It seems like this is setup as a Steam replacement, but only for a DRM-Free games, so why would you (as a creator) suggest I use this instead?
-
This also seems like there’s a world in which this is set to be a decent game hosting platform. Plans?
Thanks for showing up.

BitWarden already has lots of clients. There’s also VaultWarden for the server if you want.
This is being blown a bit out of proportion though. All they are saying is the official SDK may have some non-free components going forward. So what? It’s a private company, they can do what they want. Or the community can just fork it and move forward with a free one if they want, but it’s just not going to be in the official BitWarden clients. Hardly news or a big deal.

Well, apologies for being bluntly critical. I can offer a few constructive tips to help with writing about technical topics:
- Try starting with a simple topic flow: topic -> synopsis/purpose of why you’re writing -> background -> observations -> point<>counterpoint loop to elaborate on purpose -> closing
- Stay away from asserting your point in the title unless you’re showing definitive proof of something
- Find ways to speak to who may find your writing useful towards the beginning. “If you have a similar problem like X…”, “People who use X may find…”, or “Anyone having similar X experience may find…”. Something like that.

Anytime you see anyone post something like “THIS Is How You Do The Thing”, it should automatically be ignored. This article is no exception.
The author is making a big deal about a team of 40 people and “millions of customers”…k.
Not sure if anyone is supposed to be impressed by that, but the titular argument here isn’t a position for a small team and product, it’s making the case that “ALL THINGS EVERYWHERE ARE TOO COMPLICATED IN PRODUCTION ENVIRONMENTS”, which is just an ignorant position to take.
If this had come with some sort of metrics, tools, or workflow to back up the claim, then it would be worth reading. Nothing like that here. This is just an inexperienced person’s boasting rant with zero elaboration about what actually works for them, why, or suggestions for others facing some sort of similar situation.
There is no content here, just time wasted.

You might be looking for Nocodb

Okay, so two really big things:
-
You’re confused a bit on how network routing works. If you’re building something that bridges multiple networks (local + VPN + VPS), you need to know about how to route things to different places. You’re dealing with 3 networks at this point.
-
You might be misunderstanding how “zero-trust” and local networking fit together. Right now you have some local machines at least, AND a router. You don’t need all of your local machines to individually bridge a gap to your VPS, you want it the other way around.
If the majority of your machines are local, then make that your hub. Everything else should be a client. Adding all these individual nodes to routes in a mesh network makes absolutely no sense, and will definitely cause routing problems, if not something like ARP poisoning (we can’t see your config).
Just make the remote machine clients to your local network and be done with it.

MONTHLY?? That’s a bit much, don’t you think?
If you’re regenerating certa that fast, I can’t think of anything that’s going to secure AND easy enough to satisfy automating this.
Whatever tool you want to use to secure the contents of the cert from its initial creation, to distribution, is fine enough. If you want super easy, use an SSH/SCP script. If you want something more elegant, think Hashicorp Vault or etcd.
Ansible is probably more effort than it’s worth (plus securing the secrets of the cert), and any other config mgmt tool won’t deal with the distribution portion simply, so I’d skip all of that.

That’s really up to the software again. If you’re not technically inclined enough to run through the code, that’s fine, but you have to trust that other people are.
Go and search GitHub issues or this project by name for what you’re concerned about.
Authentication is also not security, btw. It’s just access. If you can be more specific about your concerns in your post, you may get more direct answers.

Having an HTTPS enabled server behind a proxy means the server is connecting with the proxy endpoint. That’s not how HTTPS works. If you want HTTPS enabled for a server BEHIND a proxy, you would do it at the original hand off (forward proxy), in this case meaning the Cloudflare proxy that clients connect to.
You’re seeing the errors because the proxy backend is being told to speak HTTPS with Caddy, and it doesn’t work like that.

I personally don’t find that many people are approaching me saying something like “Hey, you should be into this thing because it’s to your benefit”. That’s what insane US Christians do.
If someone mentioned a concern they were having with publicly available services, and I happened to have a self-hosted version of an alternative ready to discuss, sure.
By no means would I ever be out there trying to tell people “THIS IS BETTER. DONT YOU GET IT???”, which is where you sound like you’re coming from. It’s also not a “hobby” and it takes a lot of skill and effort to not take an INSANE amount of time for people who aren’t familiar. If you want to be tech support for a bunch of people, sure, go for it.
Totally unnecessary though.
Those were just made up brands, but you can see what I mean if you look through Amazon, eBay, Alibab…etc.
From your own tool you can see these brands stand out:
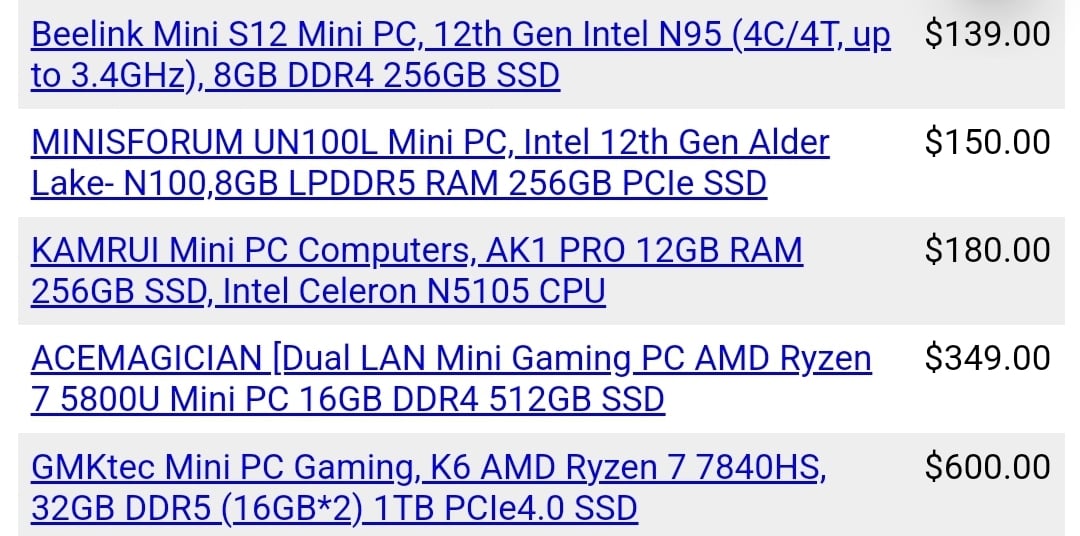
Some extra context: https://news.risky.biz/risky-biz-news-acemagic-mini-pcs-shipped-with-pre-installed-malware
‘AceMagic’ AKA ‘AceMagician’ AKA ‘AcePuter’ AKA ‘AceMini’ depending on your market.
Nice, but I wish there was a “Reputable Brand” or “Warranty” filter.
A lot of these boxes are made by the same OEM, and branded a thousand different ways under various names specifically for price fixing on large marketplace portals online - different colors, different cases, but same features without a warranty.
A lot of these fake brand names come out of companies who simply change names once they hit a certain number of bad reviews on marketplaces. Same shitty hardware, different brand name. Beelink and Minisforum are legit, but ‘KingHive Pro’ is probably made by ‘MiniKing’, and also sells things under “GamerKing”, for example.

I’m not sure, but I would be surprised if there was, especially for any sort of modern equipment. Networking hardware is really just a standard computer with a lot of specialized SoC chips specific to networking routines. So your generic home wireless router is an ARM chip, some ram, some storage, and then a wireless SoC chips, for example. Most of your enterprise type switches are basically the same Intel or AMD CPUs you’d find in a server with a ton of specialized single-purpose chips augments to offload specific jobs really fast.
So if there was a very basic beginner course to building networking hardware like, it would probably be using the concepts that 80’s hardware may have used I’d guess. Maybe try looking for someone building a modem or NIC from scratch?
You’re thinking too hard about this.
There needs to be a source of truth. LDAP is just a simple protocol that can be backed by whatever. You’re worried about the LDAP server going down, but guess what? It’s all in flat files. Go ahead and set it up in a bit repo for config management service for the server/protocol portion, and backup the DB. Easy peasy.
You can also cluster your LDAP service amongst all of your nodes if you have 3+ nodes and un-even number of them to ensure consensus amongst them. You can even back LDAP with etcd if you really want to go down that road.
You’re being paranoid about what happens if LDAP goes down, so solve for that. Any consumer of LDAP should be smart enough to work on cached info, and if not, it’s badly implemented. Solve for the problem you have, not for what MIGHT happen, or else you’re going to paranoid spiral like you are now because there is no such thing as a 100% effective solution to anything.
I think you’re missing the point of LDAP then. It’s a centralized directory used for querying information. It’s not necessarily about user information, but can be anything.
What you’re asking for is akin to locally hosting a SQL server that other machines can talk to? Then it’s just a server. Start an LDAP server somewhere, then talk to it. That’s how it works.
If you don’t want a network service for this purpose, then don’t use LDAP. If you want a bunch of users to exist on many machines without having to manually create them, then use LDAP, or a system configuration tool that creates and keeps them all eventually consistent.
Can you make it work? Yes
Should you make it work? No
It’s going to flakey beyond belief for a number of reasons, and you’ll need some pretty complex routing to make it work how I think you’re describing. I would look at using a clustered setup for your auth instead so you never get locked out due to network issues.